Software as a Service products are ubiquitous: 99% of companies use them. Businesses and private individuals alike use technically advanced tools like Dropbox, Zoom, and Gmail at zero-to-modest cost with full confidence in the security of their personal and financial information. Strict SaaS requirements cost developers millions in fees paid to security, legal, and financial experts to keep their cloud-based products aligned with multiple regulations.
If you are in SaaS product development—at the cautious ideation stage or confidently enjoying a successful series A funding—this quick rundown of SaaS system requirements will help get a better grip on the subject.
What is a SaaS Product?
The win-win nature of the SaaS business concept preconditioned the wide adoption of Software-as-a-Service model:
- Users get access to top notch technical functionality with a monthly subscription fee.
- SaaS development companies get to enjoy a huge addressable market the size of the global population times internet penetration times product interest.
- Economies, governments, and end users world over get higher quality services cheaper and faster, as businesses are equipped with SaaS tools.
This brings us to the definition of the SaaS systems:
SaaS product is a software application or platform designed with a set of functionalities, usually built on the cloud and available to consumers online for a monthly subscription fee. Popular monetization methods include freemium, pay per user, pay per transaction, or tiered pricing.
However, developing a SaaS platform is far from a walk in the park due to the many regulations that need to be studied and embedded into the business process.
Types of Requirements for SaaS Product
The major standards and frameworks for a SaaS product include legal, financial, security and technical requirements.
SaaS Technical Requirements
In most cases you will need your Software as a Service product to:
- Be cloud-based, or better yet cloud-native
- Allow for multi-tenancy
- Have microservices architecture [i.e. have loosely coupled components to avoid single point of failure, enable high availability, and fast scaling by independent teams]
- Be scalable at conception to accommodate for growth in case of rapid traction [Dev.Pro observes FinOps best practices from early stages]
- Have vigorous IAM (identity and access management) features with ABAC or RBAC [role-based access controls], two-factor authentication [2MA] or multi-factor authentication [MFA]
- Up-to-the minute application security features with data encryption, firewalls, penetration testing, etc.
- Complex payment and subscription module that may be amended on the go as monetization model evolves.
Due to the abundance of financial data, confidential corporate information, as well as other PII, these software products are a prime target for malicious agents. These are fundamental security requirements for SaaS:
Security Requirements for Software as a Service Products
In the ideal scenario, DevSecOps principles will be adhered to from the stage of MVP development. In the worst-case scenario, right after the MVP is approved and the next stage of high-fidelity design and SaaS app development is financed.
Businesses strive to ensure SOC 1 and SOC 2 compliance and OWASP’s guideline observance, like OWASP development, testing, code review guides, and application security verification standard [ASVS].
Multiple data centers, continuous penetration testing, robust device authentication, and regular security audits are among the critical focus points in Software as a service security.
These SaaS security requirements are in no way exhaustive, but they lay a foundation for the extensive network of standards and frameworks aimed at securing SaaS applications.
Legal Requirements
The legal team has a sizeable workload when establishing a SaaS company.
First, any company is expected to be compliant with these basic regulations:
- GDPR (General Data Protection Regulation)
- CCPA (California Consumer Privacy Act)
- HIPAA (Health Insurance Portability and Accountability Act)
Second, throughout the cycle of forming a legal entity, becoming a tax payer and an employer, getting financed, forming a legal framework of cooperation with your clients, or establishing IP rights, a SaaS startup is expected to produce a number of documents, for example:
- Certificate of Incorporation
- Bylaws
- Stock purchase agreement for founders
- Non-disclosure agreements
- Employee offer letters
- Technology assignment agreement
- Inventions and consulting agreements
- Stock option plans
Not to mention a number of more templated documents for the website, like these SaaS legal requirements:
- Privacy policy
- T&Cs
- Return policy
- Disclaimer
- Cookies policy
- End-user license agreements for SaaS
- Acceptance of new terms and conditions notice
Financial Requirements
Depending on your company’s SDLC stage, different layers of financial requirements apply to your business on top of the general legal requirements mentioned above.
- PCI DSS [Payment Card Industry Data Security Standard] is one of the major frameworks. This regulation is designed to streamline the protection of financial data and transactions across all online businesses.
- SaaS sales compensation.
- Monetization strategies and their implementation is another critical financial requirement for a SaaS business.
- Exit financial agreements may include acquisition, buyout, liquidation, and IPO.
Naturally, taxation intricacies are another layer to the financial and legal foundations and depend on your company’s tax registration.
5 Mission-Critical Requirements for SaaS Product
The number and complexity of SaaS security standards alone is considerable, so we are providing a few of the high-priority SaaS regulatory requirements here:
Regular Internal and External Audits of Controls For Data Security
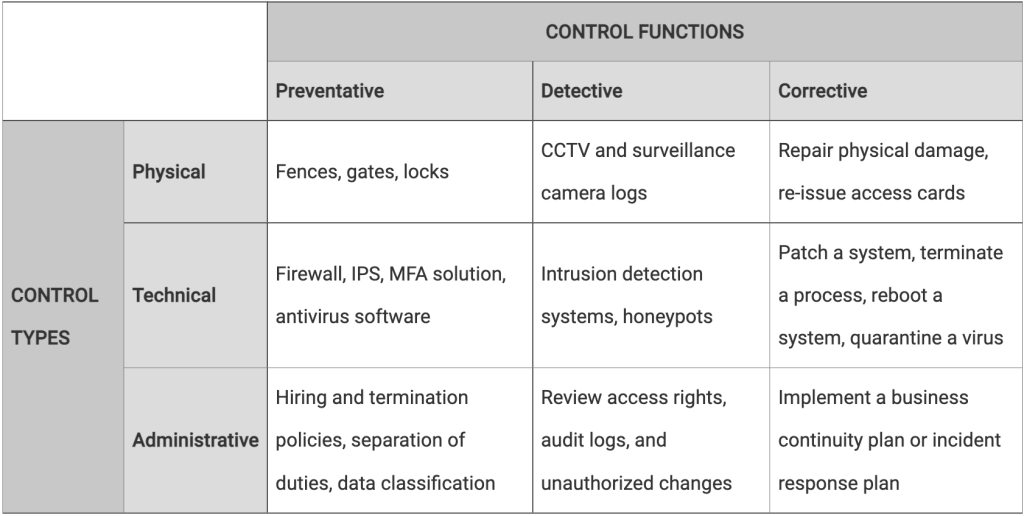
Physical, technical, and administrative controls need to be established, maintained, and monitored in a healthy, compliant Software as a Service company. They are designed and subdivided into preventative, detective, and corrective functions, as the controls expand their reach into different phases of the SDLC. See F5‘s comprehensive table below for examples of these security controls.
High Availability as a Survival Precondition
Microservices architecture is not for everyone. But if you are in the SaaS business, you cannot afford much downtime, or the avalanche of poor ratings leading to app un-loads?
Scheduled software updates and statistically predictable unscheduled downtime are limited to 99.9%. That is, 99.99% availability sealed into SaaS agreements, as a rule of thumb.
Data Storage and Data Centers Diversification
Some of your company’s workloads may require processing ASAP and some will be for auditing purposes only; some of your clients might be in China and some in Canada; and some of your data centers are physical and some are on the cloud.
It is best practice in 2022 to diversify your data centers as much as possible, to go for hybrid solutions when part of your data are stored and processed privately on premise, and you have multi-cloud solutions distributed in different geo zones, with robust DR and backup plans.
Not only does such diversification lower the chance of downtime, eliminating the single point of failure, but it’s also good for your cloud cost optimization.
Robust IAM: Device Authentication 101
Identity and Access Management are a big part of every security compliance framework, like HIPAA/HITECH, ISO, Privacy Shield, PCI DSS, NIST Cybersecurity Framework, and SOC2.
SaaS products are a prime target for bad actors and the average cost of an IAM breach to businesses is a staggering $4.4 million.
Maintaining best practices in DevSecOps procedures is critical to ensure full compliance with last-minute standards of authorization, identification, authentication, access governance, and accountability.
A zero-trust approach, conditional access management, and MFA are just a few of the key milestone requirements for cutting-edge IAM practices.
Penetration Testing
Ethical hacking can reveal some basic bugs as well as deeper vulnerabilities. White box, black box, or gray box tests allow QA experts to check newly released features, cloud services, third party integrations, API, infrastructure, and services.
Test automation enables DevSecOps early in the SDLC at a reasonable cost, reducing cost and human effort in the process.

Ready to Launch?
We have only discussed some basic SaaS compliance requirements in the early stages of product development. But SaaS also has many client devices requirements for SaaS, team structure standards, licensing and IT requisites to adhere to, that we haven’t covered.
So, when launching a SaaS product, it’s critical to rely on professionals to guide you through the legal, technical, IT, and security stages.
Dev.Pro has earned ISO/IEC 27001 certification, the model in security standards. Our application security engineers apply this knowledge to assist our clients in becoming compliant with PCI DSS, GDPR, SOC2, and other major frameworks.
Our outsourced IT team works on other components of legal compliance for SaaS, helping businesses create a continuity plan, DR docs, and implement monitoring and logging best practices to ensure audit compliance.
Looking for a software development partner with a solid background in SaaS requirements management? Talk to our tech-savvy sales team.
SaaS Requirements: Frequently Asked Questions
The three most important legal SaaS requirements are GDPR, CCPI, and PCI DSS.
The three critical technical requirements for Software as a Service products are robust IAM, cost-optimized scalability, and high availability.
You can build a SaaS product with the help of no-code platforms like Configure.IT or Bubble.is. Alternatively, you can hire a software development partner that will take care of all of the coding, design, testing, deployment, and more.